Fast Public Key Crypto and Curve25519
Sending messages without someone in the middle being able to read them
Assumes someone in the middle can read (encrypted) message
- Wifi
- Radio
- Intercepted messenger
Middleman may try to forge/tamper with messages
Steganography: grape juice

Steganography: blinking
Applying a reversible transformation to a message
Usually involves a secret key
Example: One time pad

Example: SIGSALY

Stream cipher inputs:
- 32-byte secret key
- 24-byte nonce
- 64-byte block "counter"
Without it, ciphertext is identical
Imagine SIGSALY twice

What if you want to accept messages from anyone?
Basics
- Alice generates secret key (
SKalice)
- Alice computes public key (
PKalice)
- Bob generates secret key (
SKbob)
- Bob computes public key (
PKbob)
Alice, Bob exchange public keys only
Basics, cont'd
- Alice computes
f(PKbob, SKalice)
- Bob computes
f(PKalice, SKbob)
- These produce the same key
- Use symmetric encryption with that key
Key Math Points
- Need
f with the magic property
- Given PKbob, hard to find SKbob
Alice's public/private keys
Bob's public/private keys
Alice computes shared key
Hard to reverse
- Given
A (13), find a
13 (mod 37) = 5a
- Or
13 = 5a (mod 37)
- (Discrete logarithm problem - hard!)
Pick a number (mod 37)

Which way does this door open?

Which way does this door open?

Bad design has consequences

Victoria Hall
- 1,100 children rushed toward lobby
- Lobby door opened inward (toward stairs)
- Bolted so one child could pass at a time
- Front children were trapped, crushed
Crash bars became law

Don Norman

Prone to misuse: JWT
small subgroup attack
Curve25519: deliberately chosen to avoid small subgroup attacks
Generating a private key
- Generate 32 bytes of random data
byte[0] = byte[0] & 248
byte[31] = byte[31] & 127
byte[31] = byte[31] | 64
1,2,4,8 is the only subgroup
byte[0] = byte[0] & 248
Floating point math works well with Intel registers
Add/mult mod 2255 - 19
is fast to compute
Alice's public/private keys
Array lookups are not constant time
Array lookups are not constant time
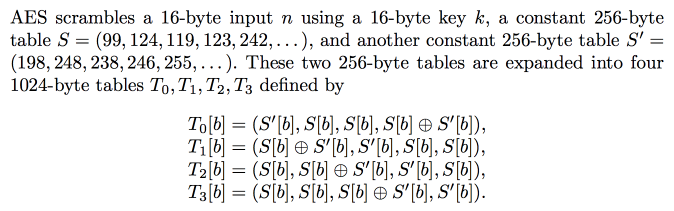
Compute values in pairs
x[b] (b ∈ {0, 1})
x[b] = (1 - b)x[0] + bx[1]
Paper ships with assembly implementation
Thanks!
Kevin Burke
These slides are available at:
←
→
/
#













